
Technical Implementation
Socially interactive deployment of mobile agent software
Implementation of the metamesh requires the deployment of the mobile agent software. The mobile agent serves three specific functions that together, enable a process of socially interactive deployment.
- Users form an adhoc network to browse and navigate metadata in their proximity.
- Users are enabled to tag each other with metadata within the adhoc network.
- Users grow the network by deploying the mobile agent software to tagged devices.
The process of socially interactive deployment is enabled by these three components as illustrated in the following diagram. The software performs tasks between the three specific user functions.
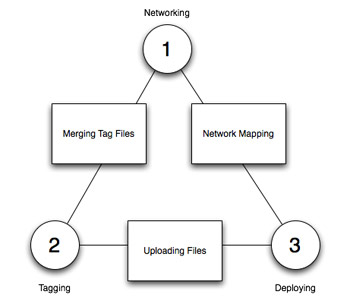
- 1-2 Merging and sharing of tag files over the network
- Tag files are transmitted reciprocally
- Each device compares the new tag data to its current network
- Each device merges the new tag data into its resident tag file
- 1-3 Active devices create a network map showing device locations and status
- The agent creates a list of connections with signal strength data
- The connection data is transmitted to the other connected devices
- Each device appends its connection list with signal strength data from the other connected devices
- The signal strength data is used in a vector map algorithm to locate the detected devices in space
- 2-3 Uploading of software to tagged devices
- A new device is detected without a mobile agent installed
- Its identity is compared with the tag data
- An invitation file is bundled with the pertinent tag data
- The file is transmitted to the new device
- The new user is queried for installation
Budget
- $10000.00 One network programmer for three months.
- $10000.00 One user interface designer for three months.
- $10000.00 One application programmer for three months.
- $10000.00 One project manager for three months.
- $4000.00 To buy a range of bluetooth enabled smart phones, which we can use to ensure compatibility.
User Stories
- Scenario 1
- User_x recently downloaded Meta Mesh upon receiving and invitation and learning that he had been tagged by a Meta Mesh user.
- Sitting in a crowded cafe, user_x viewed a bunch of tags on his display.
- One of the tags seemed specific to her profession.
- Clicking on the tag, user_x was able to see a rough location of the user associated with that tag.
- After a few seconds of browsing, she recognized the other user from a business convention that they both attended.
- Scenario 2
- User_y has been using Meta Mesh for a while.
- He and his friends have been tagging each other with extraordinary labels.
- Over time, he started to encounter those tags even if he couldn’t see any of his friends around.
- Wondering how the tags deployed, he inferred that these people must be friends of his friends.
- Scenario 3
- User_z, after installing Meta Mesh, was enjoying to tag strangers around him.
- He was not interested in reading others tags, because it seemed too subjective, too personal and unreliable.
- Yet, viewing tags he authored on the display more often than he expected made him to think about these strangers.
- Even in a big city, the daily life’s routine kept some group of people within same circles. Otherwise, he shouldn’t be seeing his tags that often.